Cybersecurity Terms: TTPs
And why they're so important
TTPs is a term that is widely used in cybersecurity. It is used heavily by cyber teams involved in cyber threat intelligence, threat hunting, red teaming, vulnerability management, and just about across the board. It stands for Tactics, Techniques, and Procedures, and refers to the TTPs used by attackers - and more often to adversary groups as opposed to lone wolf attackers.
The image at the top of this post is pulled from MITRE ATT&CK. It shows just a slice of the home page for ATT&CK - showing four tactics (Execution, Persistence, Privilege Escalation, and Defense Evasion) and some of the techniques associated with each tactic.
ATT&CK provides a wealth of information on TTPs; it is widely considered the single best source for this data and is freely available for anyone to make use of. It collects and organizes data from real world attacks. MITRE themselves introduce it like so:
MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
ATT&CK is one of the most useful resources we have available to us as defenders in the cybersecurity space. It deserves a post, or a series of posts, to do it justice - and I will look to write more on it soon.
Why Do We Care About TTPs, How Can We Use them in Cyber Defense?
There are a number of reasons why understanding TTPs is valuable for our cybersecurity Blue Team (defenders) efforts. This is a short list of some of those reasons and of some of the best ways we can put this understanding to use in crafting our defenses:
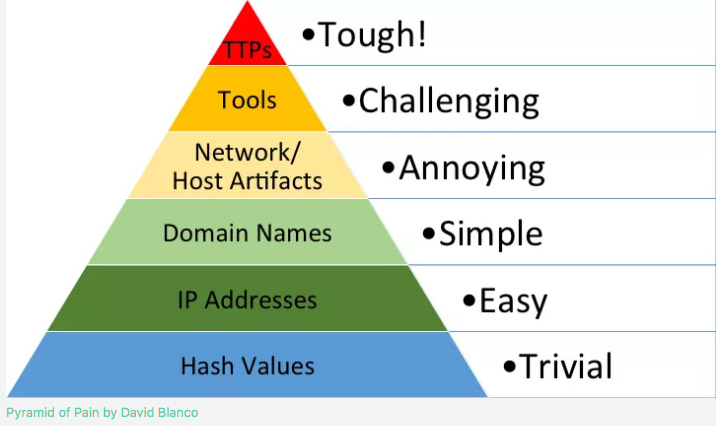
Make Life Harder for the Bad Guys: TTPs are hard to change! This is shown in the image above and said much better by David Bianco, who introduced this idea:
The Pyramid of Pain is a conceptual model for the effective use of Cyber Threat Intelligence in threat detection operations, with a particular emphasis on increasing the adversaries' cost of operations.
Threat Modeling and Threat Hunting: Understanding the TTPs that are most successful, or that are trending, or that are used in attacks against specific types of organizations, is a great starting point for being better prepared to face those attacks. This can be useful in threat modeling based on the TTPs, and also in threat hunting for indicators of their usage in our environment.
Cyber Risk and Controls Assessments: Awareness of TTPs can and should inform our cyber risk assessments and security controls assessments/audits. With controls assessments in particular, we can look to identify to what extent our existing security controls give us the capability to detect and/or prevent an attack using specific TTPs, and where we have gaps. The screenshot below from ATT&CK shows the techniques, sub-techniques, and a few of the procedures from a tactic used in defense evasion and persistence, and offers a wealth of detail that can be leveraged by defenders.
Adversary Emulation: Adversary emulation is a follow-on or level up from identifying our gaps in security controls and defenses. It allows us to put our controls and our security tools to the test. It does what it says on the box; letting us mimic the second T (techniques) and the P (procedures) in TTPs and see how successful - or unsuccessful - our systems are against them.
Finally, I think there are a lot of sports analogies that speak to why TTPs are so important in cybersecurity. A boxer who puts in the time to know his opponent’s style and where the opponent looks vulnerable, ups their chances of winning their bout. In football, baseball, and most team sports, it’s always a big advantage how an opposing team operates and to practice ways to nullify their strengths and take advantage of their weaknesses.