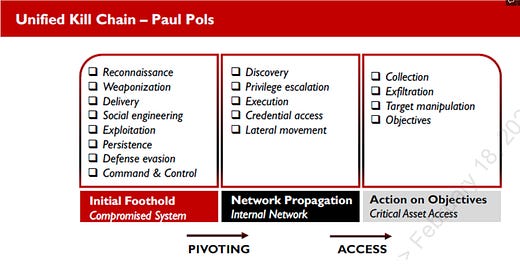
This week I’m sticking with the theme of using AI to help with educating the cybersecurity blue team. Today’s topic is credential theft and lateral movement techniques. The diagram above shows that these techniques live right in the center of attacking success in the Unified Kill Chain, created by Paul Pols. They are crucial for an attacker to be able to achieve their goals and have the most success in their attack.
In a Windows environment, one of the biggest goals - some would say a “game over” level moment - is obtaining domain admin credentials. These are effectively keys to the kingdom in a Windows network. Bloodhound is a top tier penetration testing tool that helps map out the path from an attackers’ initial foothold in a Windows network (often attained by getting one user to click on one bad thing in a phishing email) to getting domain admin credentials - like so:

The far left of the graph shows the initial, lowest level, user accounts where a foothold has been obtained, and then moving from left to right shows the shortest path to the domain admins group - and domain admin accounts ripe for credential theft.
My AI Copilot for this exercise …
Is Claude 3.5 Sonnet, which was also my copilot last week, looking at Living Off the Land attack techniques and detection and mitigation strategies that can be employed against them.
My prompt to Claude was:
Can you create a concise but detailed text outline of how the Bloodhound penetration testing tool works, and then a diagram of which security solutions can address being resilient to the sort of attacker discovery techniques used within Bloodhound
Claude produced a good outline in less than 30 seconds, but it needed a little more detail on the two primary attack elements, so my follow-up prompt was:
Can you do this again with more focus on credential harvesting and theft within the outline and the diagram
The result was a stellar outline:
Next up was the diagram. This required quite a lot of prompt tweaking and being more and more specific about what I was looking for - because Claude was generating diagrams on a dark background with very small elements and even smaller text that was near impossible to read without several levels of zooming in. In the end I asked it to create a diagram like a Visio diagram. The result is not really much like a Visio diagram, but it is easy to read and shows some good defensive strategies against the credential theft and lateral movement elements of an attack:
Claude did a superb job again today, and I need to credit the particular feature of Claude that I worked with again:
The specific feature of Claude (in its paid-for Pro version) I used here is called Artifacts. Here’s a little slice of the description of Artifacts from Anthropic (the makers of Claude):
Artifacts allow Claude to share substantial, standalone content with you in a dedicated window separate from the main conversation. Artifacts make it easy to work with significant pieces of content that you may want to modify, build upon, or reference later.
And a few of their examples of what you can do with Artifacts:
Documents (Markdown or Plain Text)
Code snippets
Websites (single page HTML)
Scalable Vector Graphics (SVG) images
Diagrams and flowcharts
Interactive React components







Thanks, Patrick! As Mr Spock would say..."fascinating"